Digital Signage Software
Solutions That Will Transform A Business
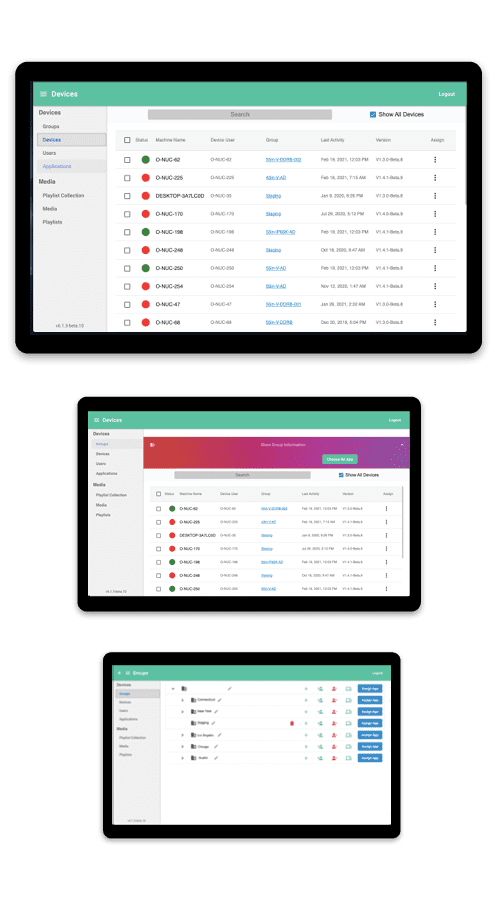
MetroClick Manager & Device Hub
Digital Signage Solutions Featuring All-In-One Content Management to Manage All Digital Signage
Configure and manage all of your digital signage displays from a single,client-specific, secure web-portal. This ensures that your digital network is secure and scalable to meet your needs.
MetroClick Manager (MCM) digital signage software allows you to easily group and assign your devices to manage everything from your entire signage portfolio to store specific signage to each individual display. This allows you to easily segment and specify content across your entire network.
POS Software
Enhance The Shopping Experience with Software Digital Signage Solution
Let MetroClick digital signage solutions turn your in-store ordering process into a seamless interactive experience.
No longer worry about getting the customers’ order wrong or lengthy check-out lines, our electronic signage systems or self service kiosk offer a robust and secure ordering platform with built-in payment integration.
Wayfinding Software
Software for Digital Signage- Connect & Engage With Your Location
MetroClick digital signage software specializes in creating interactive maps and directories for public large format touch screen displays and wayfinding kiosks.
The perfect solution for a mall or high traffic environment. Let us map out your property, or turn your existing maps into a fun and useful interactive experience.
Standard Wayfinder features include:
- Interactive Map
- Real-Time Directions
- Listings of Locations and Brands
- Directory of Events
- Live Announcements
Directory Software
Simple & Effective Digital Sign Software Solutions
Display more than simple text with an interactive directory using our display board software. Take advantage of a large format display by integrating company logos, slideshows and more.
Our Interactive Directory App is loaded with the following features:
- Custom Branding and Imaging
- Interactive Company Logos
- Building and Facility Information
- Building Announcements
- Time/Date
- Weather
- News Ticker
Advertising Software
Real-Time Content
MetroClick has created created a software platform to manage and distribute digital advertising for touchscreen and non-touchscreen displays.
Advertising displays can be used as a stand alone product or integrated into any other application.


Check-in System Software
Easy & Secure
Check-in kiosks are great for hotels, hospitals, restaurants, and retail applications. These systems enhance operational efficiency by minimizing wait times and reducing the workload on staff. Guests can easily check themselves in, access relevant information, and complete transactions securely.
Moreover, with features like ID scanning and biometric verification, these kiosks ensure a high level of security, protecting both personal data and business operations. Transform your guest experience and streamline your operations with MetroClick’s advanced check-in system software.
Contact MetroClick today to learn more about how our check-in kiosks can benefit your business!
More Information
WHAT IS DIGITAL SIGNS SOFTWARE?
As one of the top digital sign companies, we create reliable digital signage software to broadcast high quality multimedia in public places so as to effectively deliver information or product’s advertisement.
Our cloud-based digital signage offers ease of management and dynamic display capabilities, making it an ideal solution for educational institutions. Additionally, our software includes customizable templates, allowing users to tailor layouts to their preferences and requirements.
This information is played on a digital screen usually in the form of a computer mounted on big bright digital devices like plasma or LCD display.
Our signage digital software solution is classified into three categories :
Content Management system (CMS)This is where the digital signage player sources the content from. You can upload things such as images, videos, and graphics where the software will display them accordingly on the display screen. The CMS helps in creating and managing digital signage content using intuitive layout editors.
Digital Signage Player Once you have uploaded your content into the CMS, your digital signage player will then receive them via the network and broadcast them to a digital display. The player can also be part of a digital signage network for advertising purposes.
Digital screen. The digital screen works with the digital signage player wirelessly to manage and broadcast your visual content. The digital screens vary in price, functionality, size, quality, and durability.
WHY YOU NEED DIGITAL DISPLAY SOFTWARE and SIGNAGE ADVERTISING ?
According to a survey done by consumers, they find digital displays, with their dynamic and interactive nature, to be the most engaging, mainly video display. Engaging content, including images, videos, text, graphics, animations, and social media integrations, is crucial for driving audience interaction and performance. It was concluded that video marketing is highly effective in driving buyers to your business.
5 Benefits of Our Digital Signage Display Solutions
There are many benefits associated with a digital signage software solution which help to drive profits for your business.
- Compared to physical prints, the digital display is super fast and cost-effective in updating and delivering content.
- Digital advertising can reach multiple places in an instant. Buyers can see your messages whether they are in the grocery store, a restaurant menu board, or gym digital signage solution. Digital advertising can also be displayed on multiple screens across various locations.
- Digital signage hardware like touch screen kiosks allows interaction with your consumers and further brand awareness. They can look up for more details and simply check-out themselves during purchases.
- You can provide entertainment value which will be engaging and enhance the customer experience. You can also remotely manage content updates and scheduling, making it convenient and efficient (see digital signage for banks).
- Through variety of operating systems that our digital signage solution works with, you can transmit anything to the digital billboard software which ranges anything from photographs, social media feeds to advertisements, meal changes to a menu board, etc.
Contact us today to discover innovative ways we can customize digital signage to your organization’s needs.
The Latest in Digital Cloud Based Signage Solutions
No matter the size, industry or market – MetroClick realizes that no two brands are created equal. As leaders in retail touch screen technology, we specialize in digital signage platforms that integrate with other software and tools, emphasizing their importance in creating, measuring, and aiding in decision making for digital content and campaigns.
Ready for Electronic Signage Solutions for a New Era?
Additionally, our solutions enable the creation of engaging touch-screen kiosks that link to web pages. We specialize in brand and/or unique product specific software that uniquely showcases your brand by an engaging experience. We create quality digital sign solutions (rent digital sign, buy digital sign) that are sure to impress clients and customers.
SOFTWARE & SOLUTION FOR PAYMENT
MetroClick digital payment software allows users to explore various products and product configurations through the interactive digital display.
Directly from the device the user has the ability to make a purchase with a single tap of their mobile device. API payment integration allows for on-demand check out with a credit card, Apple Pay, or Android Pay.
Utilizing our MetroClick kiosk management software paired with a MetroClick kiosk, setting up your digital shopping experience is an easy out-of-the-box solution.
DIGITAL DISPLAY BOARDS SOFTWARE AND CONTENT DEVELOPMENT SOLUTION
Make use of our digital advertising boards and customized signage platform to re-purpose existing brand content or develop new content to display on an interactive platform. You can create and schedule display content from various devices using a web CMS.
Content can range from quizzes, games, interactive commercials, promotional video or static content, directories and digital wayfinding maps.
SOLUTIONS DIGITAL SIGNAGE SOFTWAREs FOR CONCIERGE SYSTEMS
MetroClick’s custom concierge digital signage software systems allow guests to explore local activities, send navigation directions to their mobile device, check the weather, learn about upcoming events, buy merchandise, make reservations or place service orders.
For more information, see our work in hospitality.
Contact Us
for Solutions
Have questions? Interested in a quote or RFP? Contact us today and one of our specialists will follow up ASAP!
California
804 Anacapa Street
Santa Barbara, CA 93101
Florida
7630 NW 25th ST
Suite 2A
Miami, FL 33122
Metroclick Offices
T: 646-843-0888
New York
239 West 29th Street
Ground Floor
New York City, NY 10001