Interactive Directory
Discover the interactive touch screen directory monitor & kiosk
The MetroClick interactive directory displays far more than simple text.
Trusted by industry leaders to power better customer experiences
Large format digital building directory systems with real-time information display
The MetroClick large touch directory allows for incorporating company logos, weather, news, transit information and more. With an interactive directory, you have unlimited listing capabilities for your building’s tenants and organizations.
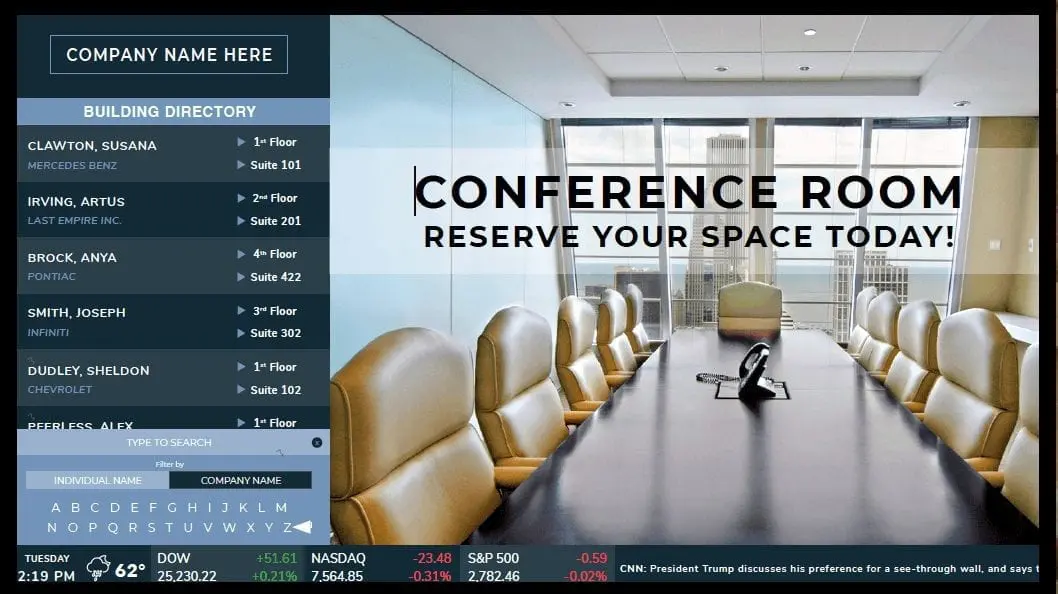
 Searchable tenant directory with company and individual lookup, plus current weather and forecast display
Searchable tenant directory with company and individual lookup, plus current weather and forecast display Live financial market data including Dow, NASDAQ, and S&P 500 tracking with real-time updates
Live financial market data including Dow, NASDAQ, and S&P 500 tracking with real-time updates Dynamic news ticker featuring latest headlines and current announcements
Dynamic news ticker featuring latest headlines and current announcements Building event management with slideshow capabilities for news, announcements, and promotional content
Building event management with slideshow capabilities for news, announcements, and promotional content Integrated advertising platform supporting both local building promotions and national ad campaigns
Integrated advertising platform supporting both local building promotions and national ad campaigns

Interactive directory kiosk system for lobbies
With MetroClick’s complete hardware lineup you can chose from a 22” to 84” large format touch screen monitor, large wall mounted monitor or our line of touch screen kiosks, to enhance your directory’s impact.
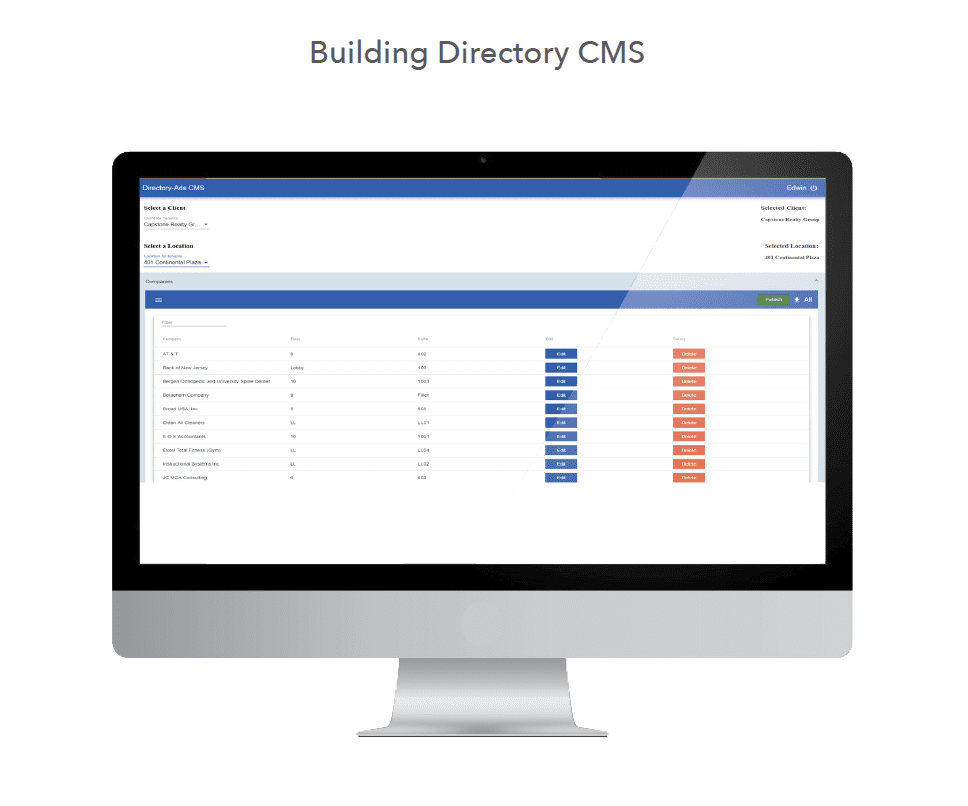
Cloud-based directory management software solutions for commercial properties
TheMetroClick directory solution allows the landlord to manage new and existing tenants, employees and advertising opportunities in real time without experiencing any of the added cost of a print-based solution. All of our clients have a dedicated Content Management System (CMS) that allows them to augment the directory and it’s on-screen content simply and effectively.
More Information
Transform Your Building’s First Impression with Interactive Directory Technology
MetroClick’s interactive directory software revolutionizes how buildings communicate with visitors, tenants, and employees. Our comprehensivedigital solutionreplaces outdated static directories with dynamic, searchable systems that provide real-time information while enhancing your property’s professional image. From corporate headquarters to medical complexes, shopping centers to educational campuses, our directory systems create efficient navigation experiences that reflect the modern, tech-forward nature of your facility.
Digital Building Directory Systems with Real-Time Information Display
Modern buildings demand more than simple tenant listings. MetroClick’s digital directory systems transform lobby displays into comprehensive information hubs that serve multiple purposes throughout the day. Ourtouchscreen interfacesallow visitors to search for tenants by company name, individual employee, or department, eliminating confusion and reducing time spent at reception desks.
Beyond basic directory functions, our systems display real-time information that enhances the visitor experience. Weather updates help people prepare for outdoor conditions, while integrated news tickers keep waiting visitors informed of current events. Financial market data appeals to business-oriented properties, displaying live updates from major indices. This multi-functional approach maximizes the value of your directory investment by serving various stakeholder needs simultaneously.
The searchable nature of our directories accommodates buildings of any size. Whether managing a small professional building with twenty tenants or a sprawling complex with hundreds of businesses, our systems handle extensive listings without the physical constraints of traditional directories. Instant search results guide visitors efficiently, while the ability to display floor plans and step-by-step directions reduces confusion in complex buildings.
Touchscreen Lobby Directory Hardware from 22 to 84 Inches
MetroClick offers comprehensive hardware solutions tailored to your building’s specific needs and architectural requirements. Our range spans from compact 22-inch displays perfect for smaller lobbies to impressive 84-inch installations that command attention in grand entrances. Eachdisplayfeatures commercial-grade components designed for continuous operation in high-traffic environments.
Wall-mounted options preserve valuable floor space while maintaining accessibility for all users, including those with disabilities. Ourkiosk solutionsprovide freestanding alternatives that can be positioned strategically for optimal traffic flow. All hardware features anti-glare screens ensuring visibility despite bright lobby lighting or sunlight from windows. Vandal-resistant glass and sturdy enclosures protect your investment while maintaining the sleek aesthetics expected in professional environments.
Temperature management systems ensure reliable operation regardless of lobby conditions, while sealed designs protect against dust and accidental spills. Every component undergoes rigorous testing for commercial environments, ensuring years of dependable service with minimal maintenance requirements. The modular design of our systems allows for future upgrades without complete replacement, protecting your technology investment as capabilities evolve.
Cloud-Based Directory Management Software for Commercial Properties
The true power of MetroClick’s directory system lies in our intuitive content management platform. Property managers access our cloud-based system from any device, making updates instantly across all connected displays. This eliminates the delays and costs associated with traditional directory updates, where simple tenant changes required professional printing and installation services.
Our software accommodates various user permission levels, allowing building management to maintain overall control while delegating specific update capabilities to individual tenants. Companies can manage their own employee listings, ensuring accuracy without burdening property management staff. The drag-and-drop interface requires no technical expertise, making updates as simple as editing a document.
Scheduling capabilities enable time-based content changes, automatically switching between different information displays throughout the day. Morning rushes might prioritize transit information, while afternoon displays could highlight building amenities or local dining options. Special event announcements, emergency notifications, and maintenance alerts can be pushed instantly to all displays, ensuring critical information reaches building occupants immediately.
Interactive Wayfinding Features for Multi-Tenant Buildings
Navigation challenges in large buildings frustrate visitors and create negative first impressions. MetroClick’s wayfinding capabilities transform confusion into confidence through interactive maps and turn-by-turn directions. Visitors simply select their destination, and our system generates the most efficient route, considering elevator locations, accessibility requirements, and current construction or maintenance areas.
Multi-building campuses benefit from our expanded wayfinding features that guide visitors from parking areas through multiple structures. Integration with parking systems can even direct drivers to available spaces before they enter the building. For medical complexes, our systems can provide directions to specific departments, doctors’ offices, or treatment areas, reducing anxiety for patients navigating unfamiliar facilities.
The wayfinding system adapts to different user needs, offering accessibility-compliant routes for wheelchair users or those requiring elevator access. Multiple language support ensures international visitors can navigate confidently, while visual landmarks help those who struggle with traditional text-based directions. This comprehensive approach to wayfinding reduces the burden on reception staff while improving overall visitor satisfaction.
Digital Directory ROI and Cost Savings Analysis
Transitioning to digital directories delivers measurable return on investment through multiple channels. Elimination of printing costs for directory updates provides immediate savings, particularly in buildings with frequent tenant changes. Properties report saving thousands annually on printing, installation, and disposal of outdated directory materials.
Labor cost reductions extend beyond printing savings. Digital directories reduce reception desk inquiries by empowering visitors to find information independently. This allows staff to focus on higher-value activities rather than repeatedly providing basic directions. Additionally, the professional appearance of modern digital directories can contribute to higher lease rates and tenant satisfaction, particularly in competitive markets where building amenities influence leasing decisions.
Revenue generation opportunities through integrated advertising provide another ROI component. Building owners can offer advertising space to retail tenants, local restaurants, or service providers, creating new income streams. The ability to sell time-based ad slots during peak traffic periods maximizes revenue potential while maintaining appropriate content standards for professional environments.
Integration Capabilities with Building Management Systems
Modern buildings operate as interconnected ecosystems, and MetroClick’s directories integrate seamlessly with existing building management systems. Connection to access control systems enables real-time updates of employee locations for enhanced security and emergency response. Integration with scheduling systems can display meeting room availability and allow instant bookings directly from directory kiosks.
HVAC and lighting system integration enables energy-efficient operations, automatically adjusting display brightness based on ambient conditions or entering power-saving modes during off-hours. Emergency management system connections ensure directories can instantly display evacuation routes, shelter locations, or other critical safety information during emergencies.
These integrations create value beyond basic directory functions, positioning the system as an essential component of smart building infrastructure. As buildings continue evolving toward greater automation and efficiency, our directory platforms provide the flexible foundation needed to accommodate future technologies and capabilities.
Contact MetroClick today to discover how our interactive directory software can transform your building’s communication capabilities. Our specialists will assess your specific needs and demonstrate how modern directory technology can enhance visitor experiences, reduce operational costs, and position your property as a forward-thinking destination for tenants and guests.